Global stocks sank Wednesday after US President Donald Trump said he was not satisfied with talks that are aimed at averting a trade war with China. Equities were also dented by poor eurozone economic data, and as Trump cast doubt on a planned summit with North Korean leader Kim Jong Un. “Trump (is) continuing to drive uncertainty over global trade,” said analyst Joshua Mahony at trading firm IG. “European markets are following their Asian counterparts lower, as a pessimistic tone from Trump is compounded by downbeat economic data,” he added. Markets had surged Monday after US Treasury Secretary Steven Mnuchin and Chinese Vice Premier Liu He said they had agreed to pull back from imposing threatened tariffs on billions of dollars of goods, and continue talks on a variety of trade issues. However, Trump has declared that he was “not satisfied” with the status of the talks, fuelling worries that the world’s top two economies could still slug out an economically pain...
Short Bytes: Tor or The Onion Router is a network that enables a user to stay anonymous on the internet and get rid of any possible surveillance, location tracking, etc. while using the internet. We can access the Tor network with the help of a modified Mozilla Firefox ESR web browser.
or or The Onion Router allows a person to browse the web anonymously by veiling the actual identity of the user. It protects the user from any traffic analysis and network spying.
Tor is perhaps the most popular and secure option available for anonymous internet connectivity. To reduce the confusion, here we are talking about the Tor network, not the web browser which is used to access the same.
History of Tor
Tor is based on the principle of ‘onion routing’ which was developed by Paul Syverson, Michael G. Reed and David Goldschlag at the United States Naval Research Laboratory in the 1990’s. The alpha version of Tor, named ‘The Onion Routing Project’ or simply TOR Project, was developed by Roger Dingledine and Nick Mathewson. It was launched on September 20, 2002. Further development was carried under the financial roof of the Electronic Frontier Foundation (EFF).
The Tor Project Inc. is a non-profit organization that currently maintains Tor and is responsible for its development. The United States Government mainly funds it, and further aid is provided by Swedish Government and different NGOs & individual sponsors.
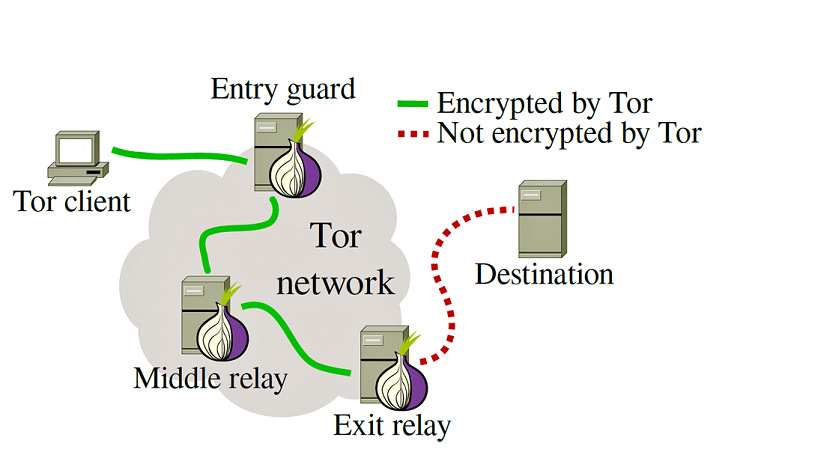
How Tor Works?
Tor works on the concept of ‘onion routing’ method in which the user data is first encrypted and then transferred through different relays present in the Tor network, thus creating a multi-layered encryption (layers like an onion), thereby keeping the identity of the user safe.
One encryption layer is decrypted at each successive Tor relay, and the remaining data is forwarded to any random relay until it reaches its destination server. For the destination server, the last Tor node/exit relay appears as the origin of the data. It is thus tough to trace the identity of the user or the server by any surveillance system acting in the mid-way.
Other than providing anonymity to standalone users, Tor can also provide anonymity to websites and servers in the form of Tor Hidden Services. Also, P2P applications like BitTorrent can be configured to use the Tor network and download torrent files.
Also Read: How To Share Files Anonymously Using Tor’s Darknet And OnionShare?
Controversies and Influence
People often eulogize Tor for the anonymity and privacy it provides to the users who want to bypass censorship, who are abused and traumatized by stalkers, and social activists who are afraid of being arrested by the authorities. It has been used by different security agencies to share confidential information.
The NSA whistle-blower Edward Snowden used Tor to leak information about PRISM to The Guardian and The Washington Post.
However, the story is not all good-good. Tor faces criticism for the reason that it acts as a medium for different illegal activities like data breaching, drug dealing, gambling, etc. Tor is also used by criminal minds to communicate over the internet while keeping their identity hidden which makes it difficult for the security agencies to trace them.
The U.S. National Security Agency (NSA) has called Tor “the King of high secure, low latency Internet anonymity.” And similar comments by BusinessWeek magazine, “perhaps the most effective means of defeating the online surveillance efforts of intelligence agencies around the world”.
Another speculation made is that Tor takes its funding from the U.S. Government which may lead to the assumption that NSA may have compromised the identities of individual Tor users. However, the executive director Andrew Lewman has disclaimed any confederations with NSA.
Is Tor Safe?
Various claims have been made to compromise Tor’s anonymity and security from time to time. The most famous one was the Bad Apple Attack in which the researchers claimed to have identified around 10k IP addresses of active BitTorrent users who were connected via Tor.
The Heartbleed bug was behind another major compromise in April 2014 which halted the Tor network for several days.
Traffic Fingerprinting is a method used to analyze web traffic by analyzing the patterns, responses, and packets in a particular direction. This technique can be used to attack the Tor network by making the attacker’s computer act as the guard.
The main vulnerability was found at its exit points where the level of security is very low as compared to the rest of the Tor network.
The main vulnerability was found at its exit points where the level of security is very low as compared to the rest of the Tor network.
Also Read: TOR Anonymity: Things Not To Do While Using TOR
How to download Tor browser?
The Tor Project Inc. has released Tor Browser which is a modification of an Extended Support Release version of Mozilla Firefox browser. The browser is portable so that it can be used from an external media and also reduces the hazel of installation. Tor Browser removes the browsing history and cookies after every use, thus reducing the risk of any cookie tracking. We can set-up SOCKS (Socket Secure) based applications to use the Tor network by configuring them with a loop-back address.
Tor Browser removes the browsing history and cookies after every use, thus reducing the risk of any cookie tracking. We can set-up SOCKS (Socket Secure) based applications to use the Tor network by configuring them with a loop-back address.
The Tor browser is available various desktop operating systems including Windows, Linux, and MacOS. You can visit this link to download Tor browser.
How to install Tor browser on Windows?
- Run the Tor Browser setup.
- Choose your desired language.
- On the next windows, choose the destination folder. Using Tor would be easy if you choose the Desktop as the destination.
- Click Install.
The setup will create a folder named Tor Browser on your Desktop. Open the folder, and run the shortcut file to use Tor Browser.
For Linux, you’ll have to extract the downloaded file either using the command line or a file extractor application.
Tor Browser for Android
Orbot – a proxy with Tor for Android devices.
Orfox – a mobile version of Tor Browser for Android devices.
The Guardian Project, a global developer community founded by Nathan Freitas, is to be credited for the development of these apps.
Tor Browser for iOS
An official Tor browser app for iOS is available on the App Store.
Tor Alternatives
Hornet is a new anonymity network that provides higher network speeds compared to Tor. I2P and Freenet are other anonymity networks which can act as Tor alternatives. Also, Tails and Subgraph OS are Linux-based distributions with built-in Tor support.
To know more about these alternatives, please visit this link.
Should I Use Tor?
Tor has proved to be an excellent medium for safe, secure and anonymous web presence available to a user at no cost. The developers of Tor didn’t intend it to become a hotbed of illegal activities, but evil-minded people have leveraged Tor for their benefits. The Tor project has led to an optimistic approach towards censorship and surveillance-free internet.
You can use Tor if you want to conceal your identity on the web or access some website that blocked in your region. But refrain yourself from doing anything that’s above the law because nothing is fool-proof and they can still catch you. Also, accessing your social media accounts over Tor can expose your identity.
Also Read: Tor or VPN? What’s Best And Which One Should I Use?
For more idea about ‘How Tor works’, please have a look at his video:
Did you find this helpful? Drop your thoughts and feedback.


Comments
Post a Comment